Everybody knows what hand hygiene is: hands are disinfected every time we enter a hospital. In the same way as germ-free hands stops diseases from spreading, password hygiene helps to prevent the misuse of credentials. Password hygiene may feel useless when the effect is not immediately visible, but it is never the less very important in the age of information society.
Password hygiene is no harder that normal hygiene. Everybody can learn it with the following simple principles:
1. Store your passwords securely

A trick to avoid storing passwords in plain-text on paper
The best would of course be to store all passwords inside one’s head, but since remembering all credentials by heart isn’t simply possible, another good option is keeping the in your wallet. People keep money in their wallets, so most of us are used to store it securely.
Passwords can be “encrypted” on paper with a simple trick: use a common first part in all passwords, for example ‘Ma55i’, which you remember by heart. Then write the last part of the password on paper, for example ‘hU8kkP’. Only you will know that the complete password is then ‘Ma55ihU8kkkP’.
Remember also to make backups of it for example by xeroxing the paper slip. Use the money analogue to choose a good place to store the backup: put the important paper in a safe.
Using paper has some drawbacks, like the need to type passwords all the time. Using a piece of software on the computer will make things easier, because then it is possible to simply copy-paste the usernames and passwords from the program. The recommended program is KeePass. It is free and open source software, its internal functioning is transparent and it is unlikely to have backdoors or other weaknesses, and the same program is available for multiple platforms, including Windows, Linux, OS X, Jolla, Android.
2. Use different passwords in different systems
It is dangerous to use the same password in multiple accounts. For example if your Twitter-password leaks and somebody can log in to Twitter using your account, they will quickly find out what your e-mail address is, and then for sure try to log into your e-mail account using the same password you had on Twitter. Can you afford to loose control of multiple accounts at the same time?
Here too, programs like KeePass help, because they facilitate the automatic generation of new passwords for each new account.
3. Use passwords which are difficult to guess
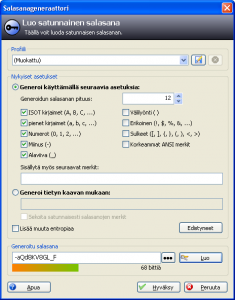
KeePass password strength meter
Password crackers always start out by trying to guess typical passwords, like horse99 or 123hound. Don’t have a weak password that is likely to be cracked by brute-force password cracking tools. A good password is complex and consists of at least 9 characters, and includes both capitals and small letters, numbers and special characters like +-.,_:;. Alternatively you can also use a less complex password if it is at least 16 characters long.
Again, KeePass helps with this too, because it has a built-in password strength meter, which will tell you it the password is strong enough, or it can even generate the passwords automatically for you.
4. Change your passwords regularly – or immediately if you think it has leaked!
If the password is strong enough, then a suitable interval to change passwords is a few years. If a password is too weak, then it does not matter much if you change if often or not. Rule number 3 is therefore more important.
In KeePass the dates when a new password was saved is automatically stored, so it can also help you see how old your passwords are.
If somebody suspect somebody peaked over your shoulder and spied on your password, you need to change it immediately. Well designed computer systems show you on login when your previous login was. For example if you return to work after a holiday, and when you log in the system tells your last visit was a few days ago – while you were still on holiday – you will notice that something is wrong and know that the password needs to be changed.
5. Never tell you password to anybody
Never ever tell your password to anybody. No administrator on any system needs to know your password – administrators can anyway always reset your account and get the password that way. If somebody asks for your passwords, it is almost for sure some kind of fraud.
The most common reason for password leaks is that users have themselves told the password to somebody who had a credible enough sounding reason to ask for it!
6. Send you passwords to the correct system and only using a secure connection
When you are about to sign in to a system, try to make sure that you are really connected to the correct system and that the connection is securely protected. A common way to steal passwords is to do a so called man-in-the-middle attack, where the user is tricked in a way or another to enter their credentials to a false system, yet the connection is passed on to the real system so the user does not notice anything unusual. For websites make sure the URL in the address bar is correct before you sign in and make sure it contains the s in the https part so that the connection is secure.
This is however not a guarantee – sophisticated attacks can make the remote system appear perfectly normal with correct address and everything, because the attack might target the underlying network infrastructure. But none the less, every user must make sure they do their own part in keeping the systems secure, and what happens after that is up to the system engineers to take care of.
Original presentation in Finnish
..is available on Slideshare:



2 thoughts on “Password hygiene – every man’s responsibility”